Advancing Threat Intelligence for an Industrial Software Provider
Modus Create strengthened threat intelligence and automated incident response for an industrial software manufacturer with its security assessment.

Table of contents
Subscribe via Email
Subscribe to our blog to get insights sent directly to your inbox.
The industrial goods and services sector has witnessed rampant ransomware attacks in 2022. A global software manufacturer in the industry wished to proactively minimize this threat. Modus Create’s three-week security assessment helped the client advance threat intelligence and automate incident response, leading to a stronger security posture.
Our Work Involved
- Documentation and Tooling Review
- System Architecture Review
- Incident Response Automation
- Threat Intelligence Consolidation
Impact
- Faster Incident Response Time
- Standardized Playbook Taxonomy
- Centralized Threat Intelligence Repository
3 Software Platforms Reviewed
2 SOAR Playbooks Enriched
In the ever-changing cyber security landscape, one of the top targeted sectors is industrial goods & manufacturing. The industry has witnessed a spate of targeted attacks in recent months.
According to a report by Digital Shadows, industrial goods and services faced the largest number of ransomware attacks among all industries in 2021.
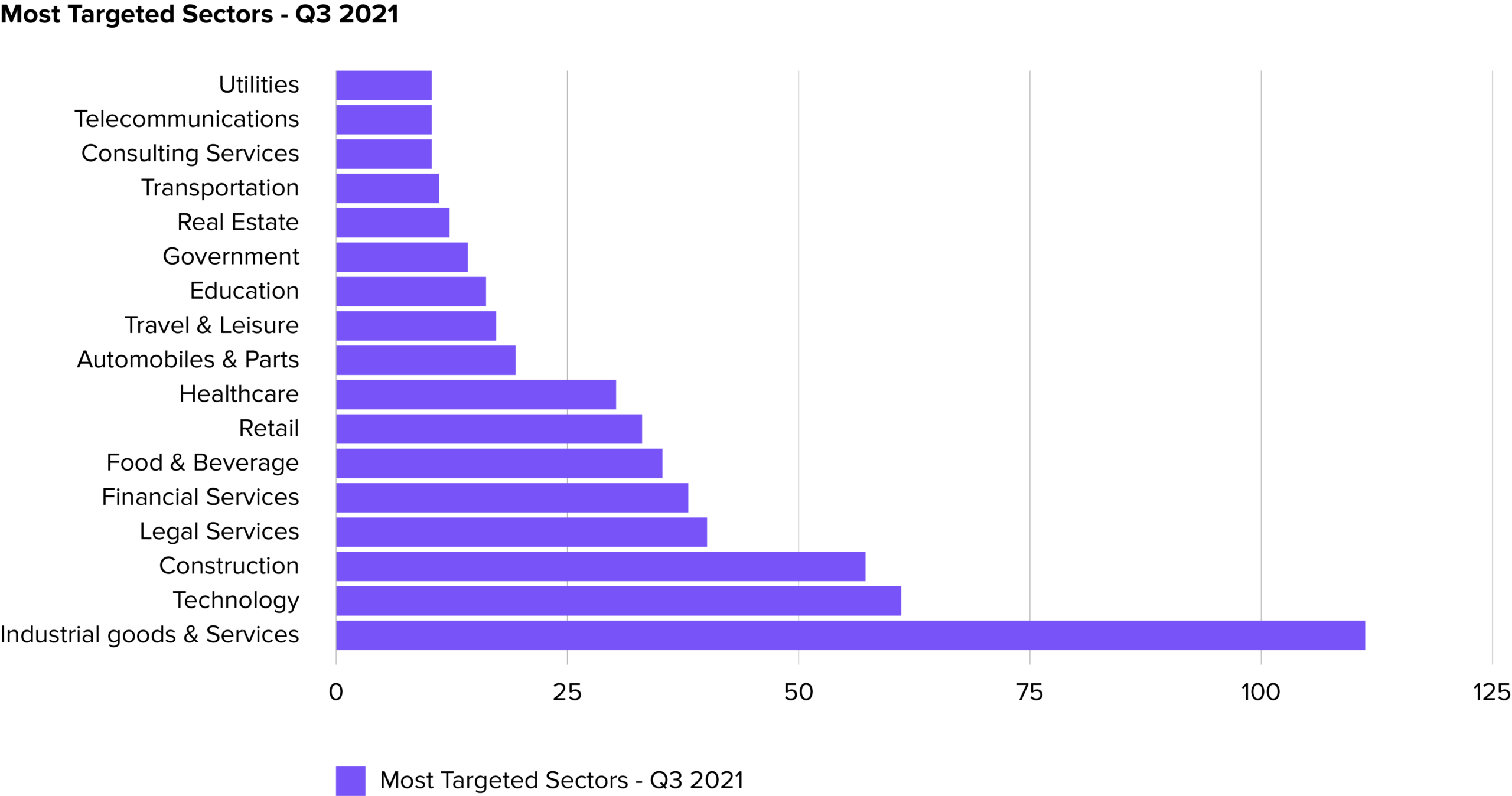
Industrial environments are particularly vulnerable because outages often disrupt their entire supply chain, directly affecting their bottom line. This makes them susceptible to paying the cybercriminals to get operations running again.
Understanding the Problem
A multinational software vendor for the architecture, manufacturing, and engineering sectors discovered communication gaps across its platforms. Moreover, a lack of standardized taxonomy made it harder for teams to categorize threats and triage data to connect the dots.
For example, some teams would classify an incident as type A while others would classify it as type C. So, when an incident would occur, occasionally, teams did not know how to share their discovery with sister teams due to a lack of standardized taxonomy. This affected the organization’s ability to form a concerted response to cybersecurity threats.
Therefore, the organization decided to correlate threat intelligence to create a centralized repository that will significantly reduce incident response times. Modus Create’s team of five cybersecurity experts joined the client for a three-week security assessment designed to leave them fully prepared to mitigate and tackle future cybersecurity threats.
The Assessment Approach
The goal of the Modus assessment process is to provide recommendations on two levels – tactical: fixing existing security vulnerabilities, and strategic: putting structures in place to avoid high-risk scenarios.
The team decided to follow a simple four-step approach:
- Meet with system owners to understand the current state and architecture
Talking to relevant stakeholders helped us understand each team’s unique perspectives, challenges, and opportunities, laying the foundation for a well-informed security assessment.
- Review all cybersecurity-related tooling policies and documentation
After the interviews, we reviewed team-specific documentation and compared it with the company’s overall guidelines, policies, and standards. This revealed a lack of documentation in certain areas and an opportunity to standardize on taxonomy to align all teams to enable better communication and understanding.
- Provide industry best practices on tools in scope and develop tailored recommendations
Along with suggesting and consolidating the toolset, our team also coached the client’s security teams on best practices in using these tools. This enabled the client to unlock maximum value for tools they had already invested in and encouraged knowledge sharing across different teams.
- Prepare detailed report and timeline of action items
We provided a timeline of action items, prioritized according to their severity, and suggested resources needed to address those items. Therefore, the client received a roadmap ripe for execution.
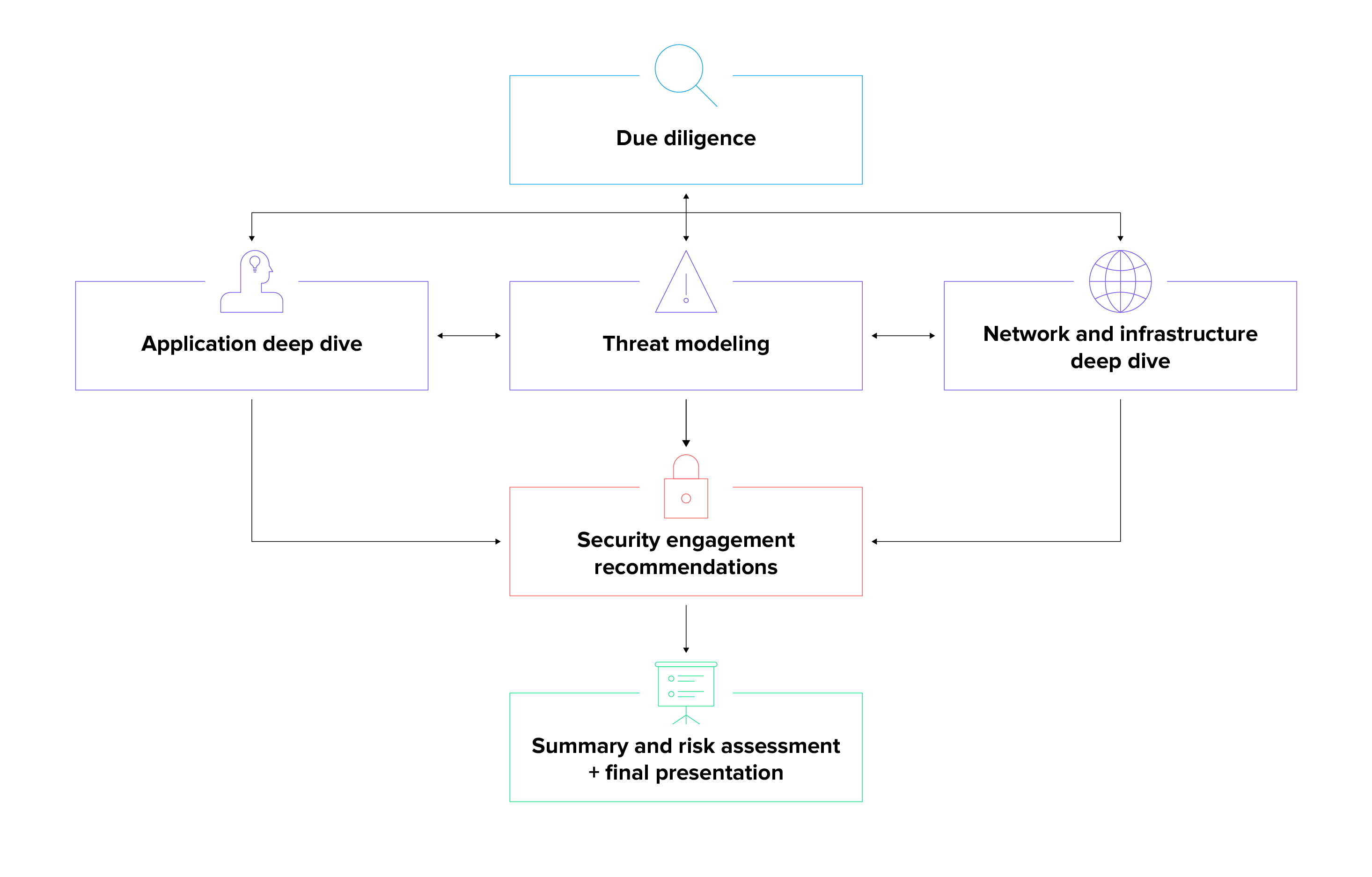
Modus Create’s Security Assessment Process
The assessment revealed that although the client had positive practices and operations in place, they could better leverage automation in security response and data enrichment through global threat intelligence feeds.
1. Threat Intelligence Advancement
Our team suggested the client utilize their threat intelligence platform’s feeds, establishing data pipelines across various platforms. In addition, the team assisted with reviewing the current architecture and outlined a representation of a proposed harmonized state between the platforms.
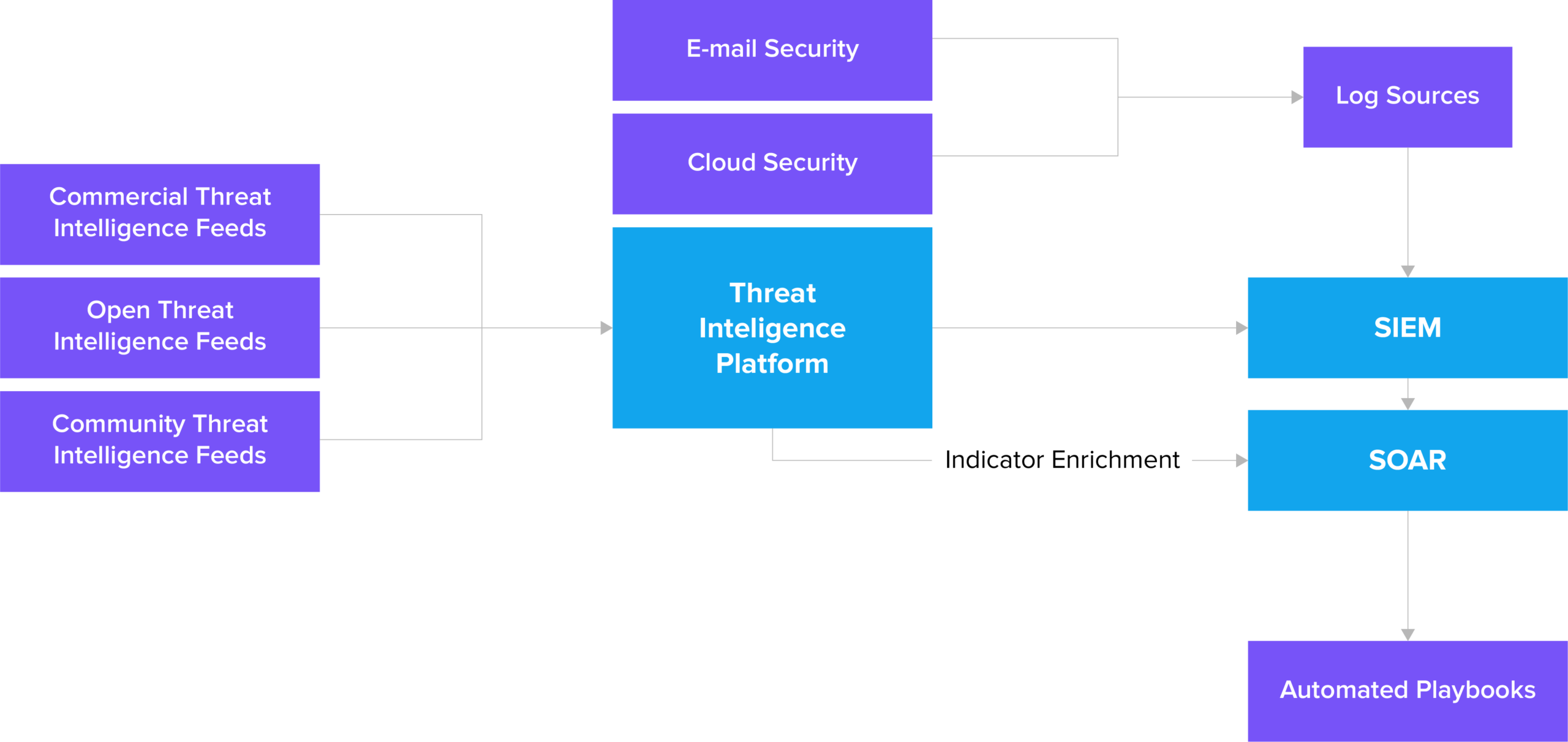
As opposed to the previous decoupled architecture, the new architecture is able to correlate data across systems enriching incident case notes with threat intelligence and enabling the development of internal threat intelligence collection from existing incidents. This allows the client to reduce threat response times and stop serious security issues in their tracks.
2. Incident Response Automation
The client’s Incident Response approach relied heavily on a SOAR (Security Orchestration, Automation, and Response) platform, which gathered metrics and consolidated investigation documentation. The team reviewed the platform’s current use-cases and architecture and provided recommendations on the following:
- Change management standards and communication for playbooks
- Organization’s current taxonomy, language, and standards to ensure incident categories align with standard definitions for all playbooks
- Integrations across security platforms to leverage connectivity updates
- Incorporating correlated updated data from threat intelligence into playbooks
- Initiating playbooks stemming from SIEM triggering a match on threat feed data
- Creating a SIEM search that correlates threat feed intel against existing web, firewall, DNS, or endpoint security tooling/logs
Impact of the Engagement
Modus Create’s cybersecurity experts converted the assessment insights into a roadmap with specific deliverables. So, the client knew not just what to work on but also how to prioritize.
The client possessed the resources to execute most of the recommendations and immediately addressed the high-priority action items. Some of our experts then embedded with their team and helped them improve and automate SOAR incident response playbooks.
With a standardized taxonomy and centralized repository, the client can now properly identify the correct event category and prioritize across teams. Everyone has access to the same data, allowing for faster communication and more accurate response to potential cybersecurity threats.
Vital Stats
- 8 Interviews Conducted
- 2 SOAR Playbooks Enriched
- 3 Software Platforms Reviewed
- 10 SOAR Playbook Recommendations
Are you interested in improving your cybersecurity? Talk to Modus. As an official AWS and GitHub partner, we have helped some of the world’s leading organizations strengthen their response to cyberattacks. Learn more about how Modus Create can identify and remediate risks to your business with our Security Assessment.
Related Customer Stories
Discover more customer stories.