Strengthening a Home Security Company’s IT Security
Modus Create’s expert multi-disciplinary team worked closely with the client’s IT department to fix tactical vulnerabilities, suggest long-term strategic changes to enhance security, and consolidate cloud environments.

Table of contents
Subscribe via Email
Subscribe to our blog to get insights sent directly to your inbox.
A leading home security company that protects over one million people in the US wanted to uncover and fix its IT security vulnerabilities. It also wished to consolidate its multi-cloud environments to reduce both cost and risk from attacks. Modus Create’s expert multi-disciplinary team worked closely with the client’s IT department to fix tactical vulnerabilities, suggest long-term strategic changes to enhance security, and consolidate cloud environments.
Our Work Involved
- GitHub source code review
- Evaluation of multi-cloud environments
- Review of DevOps infrastructure
- Short-term tactical security fixes
- Long-term strategic roadmap
- Pen testing on existing systems
Impact
- Uncovering critical application vulnerabilities
- Highlighting sensitive info that was publicly visible
- Introducing best practices of Infrastructure as Code and DevSecOps
Cost savings – $4000 per day
The first step to making anything secure is to shrug off the delusion that the worst-case scenario won’t happen to you. This requires confronting vulnerabilities rather than brushing them under the carpet.
Who can understand this better than a company that provides home security solutions to over a million Americans. The company wanted to upgrade its security posture by:
- Highlighting and fixing existing security vulnerabilities in the organization
- Consolidating its three cloud environments into one to reduce both cost and risk of attacks
They teamed up with Modus Create to perform an in-depth security review. A team comprising security experts, consultants, and engineers, along with the client’s IT department, kicked off the engagement.
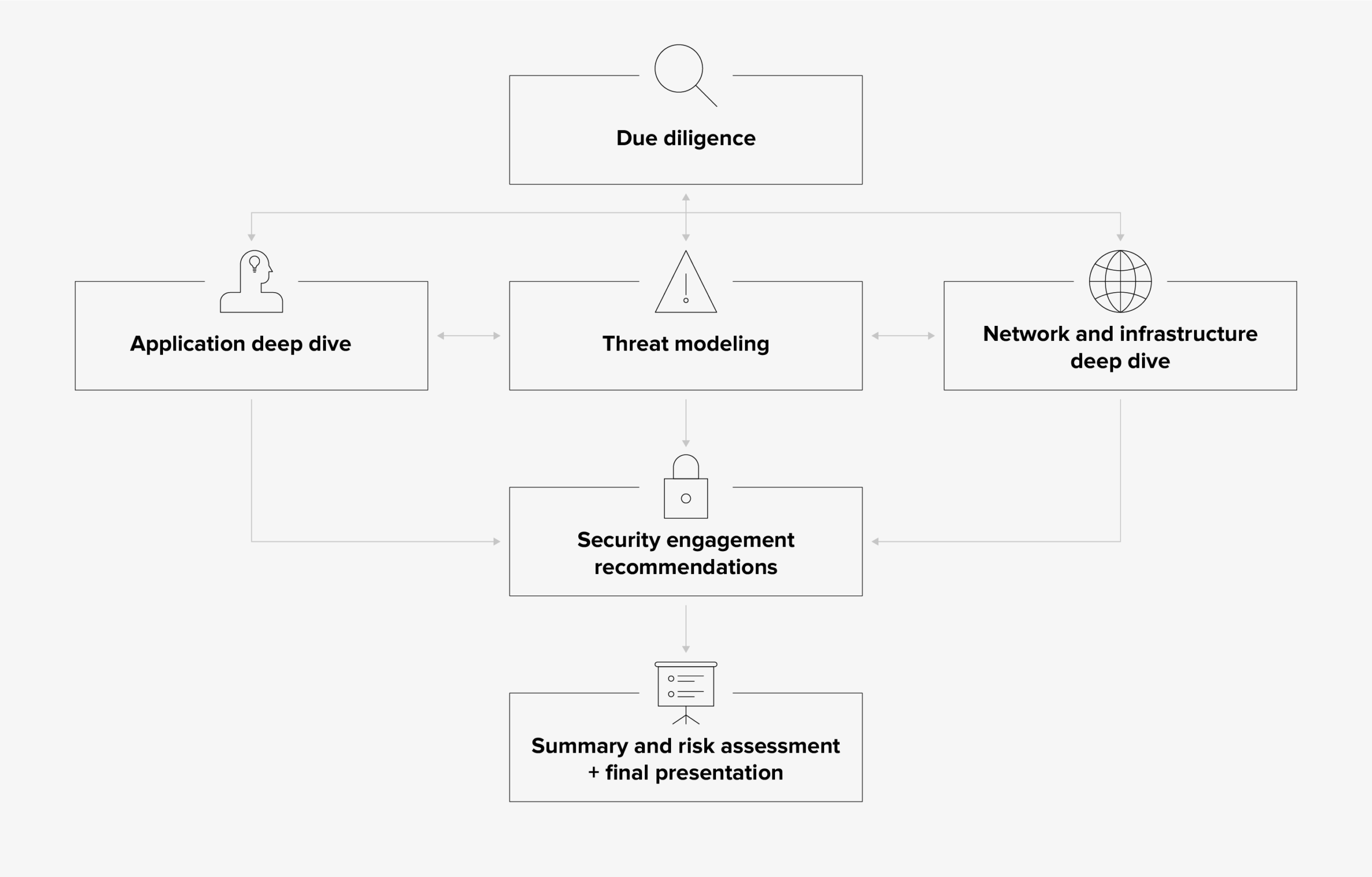
Uncovering Security Vulnerabilities
The team uncovered some critical security vulnerabilities during the first phase of their work, such as:
- Legacy Systems – The client had undergone a merger recently. As a result, there were various legacy systems in their cloud environment without any purpose. These systems were not only draining the client’s resources but also increasing their attack surface.
- Unsafe Passwords – A debug dump could reveal the client’s passwords, which hackers could use to break into their systems.
- Poor API Configuration – The API configuration in the client’s cloud environment didn’t follow best practices.
- Exorbitant Spend on Cloud – The client had accidentally spun 6 ML EC2 instances, each running at $30 an hour. The Modus team provided recommendations around governance to prevent this from happening again
Overall, the team discovered 100+ tactical security issues, out of which 9 carried very high risk. The threat/vulnerability rating was based on SANS – An Overview of Threat and Risk Assessment.
Driving Strategic Changes
A security assessment isn’t just about highlighting existing vulnerabilities and suggesting ways to address them. It also involves digging into the root causes of those vulnerabilities. Otherwise, it’ll just be a matter of time before similar or even more severe vulnerabilities appear in the future.
The client had identified one such root cause – three different cloud environments, each with its own infrastructure and unique security challenges. Additionally, the client had services and source code repositories stored on-premises.
The team discovered the following insights after a deeper review of all environments:
- One legacy cloud environment was overly complex and lacked both governance and guard rails.
- The client had deployed an incomplete monitoring program and tuned vulnerability scanning program across the three environments and source code. The use of one cloud service, where little visibility is possible, further increased this problem.
- Incomplete DevOps pipelines, including gaps in the static analysis, lack of code quality tests, and missing unit tests. The use of production data deployed in staging and QA environments of certain applications had high risk.
- Legacy and unmaintained technologies in GitHub, including Python and PHP, contained many vulnerabilities. In some instances, code still had active production credentials, embedded without any secrets scanning mechanism.
Based on the review, the team suggested consolidating all cloud environments into a single vendor.
Impact of the Engagement
The engagement provided both short-term benefits and long-term strategic insights to the client.
Just by introducing governance around EC2 instances, the client could avoid a repeat scenario of wasting up to $4000 per day. The client also uncovered some critical security risks, such as unsafe passwords, and received a clear plan to consolidate its three cloud environments.
The engagement introduced a culture of Infrastructure as Code and DevSecOps in the client’s organization. Their IT department realized the need to incorporate infrastructure and security best practices during the development process rather than treating them as an afterthought. This would help in both reducing the attack surface of their systems and the wastage of resources.
After this successful engagement, Modus teams stepped in to begin remediation work on suggested fixes and upgrading the client’s Windows systems.
Related Customer Stories
Discover more customer stories.